MultiCipher Plugin for KeePass
With Yubikey HMAC-SHA1 support
(First of all many thanks to Dominik Reichl for creating KeePass Password Safe (http://www.keepass.info) this plugin would not have existed otherwise)
For technical details check out the source repository at: https://github.com/titasraha/multicipher
Comments/Bugs/Improvements email me at support@titasraha.com
Version 2.2 for KeePass >= 2.41
MultiCipher encrypts KeePass database using 2 independent keys and 2 different algorithms instead of one. The data stream is doubled by generating a random stream and merged together to form a double sized encrypted database. It follows a method as outlined by Bruce Schneier in his book "Applied Cryptography" (Link).
1st Key
The first key is provided by KeePass which is generated at the time of database creation as usual, this key is used to encrypt a part of the database stream
2nd Key
The second key may be generated by one of the following methods
- Single Password Mode, derived from KeePass Masterkey
Although may not be the best option but definitely the easiest, there is no need to manage or remember a second key - Dual Password Mode, Generated from a 2nd PasswordA second independent password may be used to encrypt the database
- Generated from Challenge/Response from a hardware Yubikey
This option uses Yubikey hardware to generate the 2nd Key, this provides a balance of high security and ease of use
Alorithms
Currently AES-256, Twofish, Tripple DES, ChaCha20, Salsa20 are options available to encrypt either of the 2 streams.
Setup Instructions
The installation package contains all required files necessary for the plugin to work. Just copy all the files (including the subfolders) into the application executable directory.
Please Note: The package contains the driver files namely "libykpers-1-1.dll", "libyubikey-0.dll", "libjson-0.dll" and "libjson-c-2.dll" from Yubikey that should be placed in their respective 32bit and 64bit sub folders. You may also download these files directly from the Yubikey site https://developers.yubico.com/yubikey-personalization/Releases/, however these files are not required if you do not plan to use Yubikey.
Run KeePass and create or open an existing KeePass database, change the database file encryption algorithm to "Multi Cipher" as shown below, other setting may be changed as per preference.
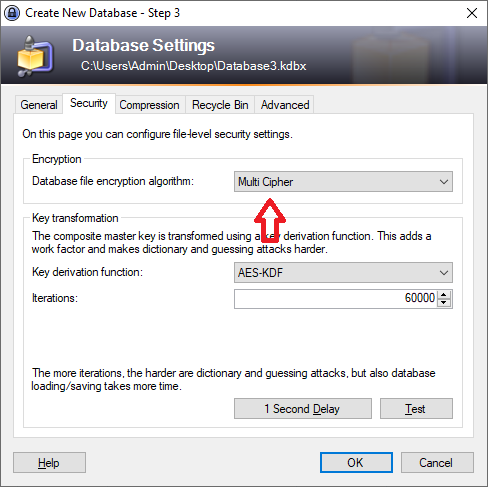
After the database is created, from the tools menu choose "MultiCipher Encryption Settings...", choose the 2 algorithms for encryption (or leave as is). By default MultiCipher uses Single Password Mode for the second key
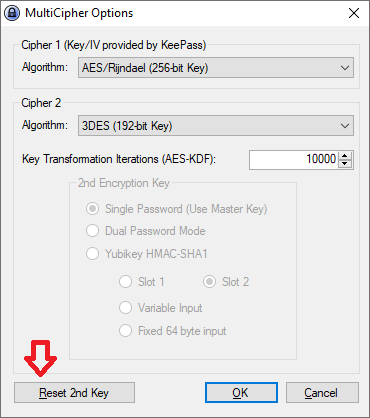
To change the 2nd Key click the "Reset 2nd Key" button. If you choose the Dual Password mode you will be ask to provide a new password for your 2nd Key. If you choose Yubikey HMAC-SHA1 make sure the options chosen matches with the configured Yubikey as described below
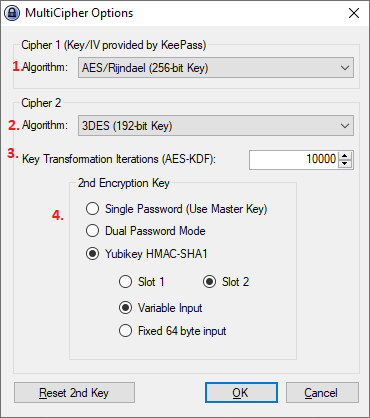
Yubikey Challenge/Response
This applies only if you choose Yubikey HMAC-SHA1 option above.
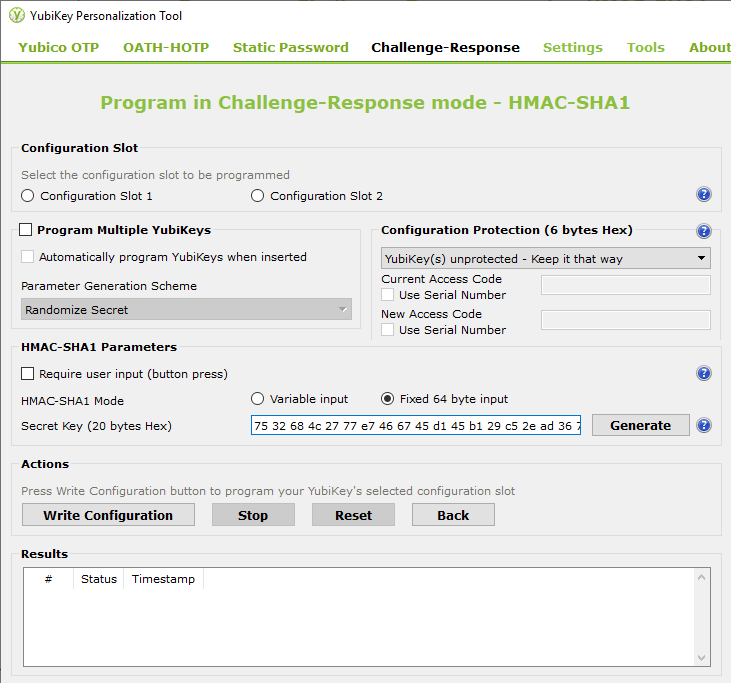
You will need the Yubikey Personalization Tool to setup your Yubikey for HMAC-SHA1 Challenge/Response (https://www.yubico.com/products/services-software/download/yubikey-personalization-tools/. As shown below for the Challenge/Response tab option, first choose the slot you would like to configure. Check on "Require user input" to wait for a tap on the Yubikey to proceed (this ensures that someone is present before the key is generated though you may leave it unchecked for ease of use).
Choose any "HMAC-SHA1 Mode", but remember the option chosen must match with the option chosen is the MultiCipher Options dialog
Secret Key - You may generate the secret key by clicking on the Generate button or you may provide your own key here. This key is never used by MultiCipher, although it is recommened that at the key is validated (see below 'Key Validation').
Finally, click on the Write Configuration to save the settings on Yubikey (More about Yubikey Challenge/Response)
Key Validation
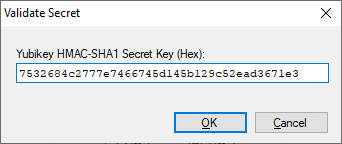 You will be prompted to validate
the Yubikey Secret Key configured above, although optional, it is a good idea to make sure that the key
generation process is working correctly. If you still prefer not to take the key out of the device ever, you
may do some trial save and load database to make sure things are setup correctly. If you choose to validate
your key, you will be asked to enter the secret key here.
You will be prompted to validate
the Yubikey Secret Key configured above, although optional, it is a good idea to make sure that the key
generation process is working correctly. If you still prefer not to take the key out of the device ever, you
may do some trial save and load database to make sure things are setup correctly. If you choose to validate
your key, you will be asked to enter the secret key here.
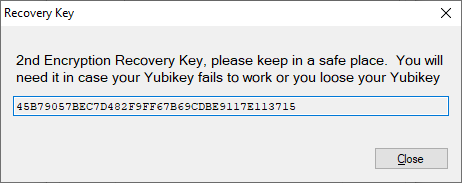 If everything goes well you will be
presented with a encryption key that will be used as the 2nd Key for the encryption/decryption process.
Please make sure you copy it and save it in a safe place, as in case of any issues with Yubikey you may use
the recovery mode to decrypt the database. Without this key there is no way to decrypt the database.
If everything goes well you will be
presented with a encryption key that will be used as the 2nd Key for the encryption/decryption process.
Please make sure you copy it and save it in a safe place, as in case of any issues with Yubikey you may use
the recovery mode to decrypt the database. Without this key there is no way to decrypt the database.
Keepass Database Recovery
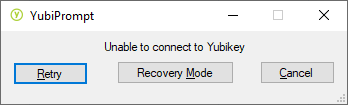 In case
something goes wrong with the Yubikey you will be presented with the following message, you may retry in
case the Yubikey is not connected. However if you have lost your yubikey or there is some harware issue you
may try the recovery mode by clicking on the "Recovery Mode" button.
In case
something goes wrong with the Yubikey you will be presented with the following message, you may retry in
case the Yubikey is not connected. However if you have lost your yubikey or there is some harware issue you
may try the recovery mode by clicking on the "Recovery Mode" button.
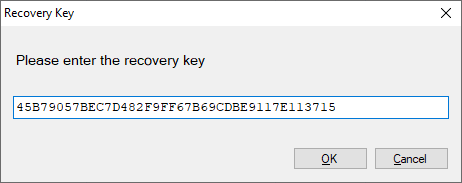 Enter the
recovery key saved in the initial stage to recover the database.
Enter the
recovery key saved in the initial stage to recover the database.
Acknowledgement
- Part of the Yubikey Challenge/Response code used in this application have been adapted from Keepass KeeChallenge Plugin work by Ben Rush
- Twofish algorithm from Josip Medved